After more than 2 years of suffering with my LG Optimus L5, which is made by the evil himself, i finally bought another mobile. You might be thinking it must be the latest trendy one. But no. It is among the cheapest phone on the market right now. I bought it for Rs 3048. I’m totally satisfied with it.
Auto brightness
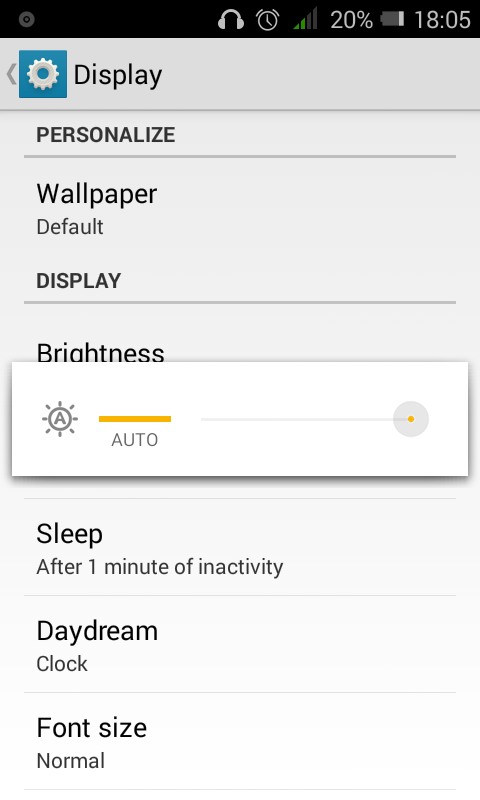
Yep. It has a light sensor integrated.
Camera
From the lock screen, i can just swipe left and the camera opens in less than 2-3 seconds. The camera quality is very usable. It is 5MP actually and also has a front VGA camera which can be used for video calls. Can’t be used for selfies though (not a fan of selfies anyways).

720p video recording
The rear camera can record codes videos by 1280x720p which is not bad at this price.
Dual Core 1.3GHz, 500MB
Moving from a 800MHz CPU in my old LG Optimus L5, i find this phone to be a breeze. Browsing the Web, launching apps, multi tasking is no issue. I remind you again that i was previously using the most crappy phone ever made. The RAM seems OK with Facebook, Gmail, whatsapp, KDE Connect, music running in the background while doing other stuffs in the foreground.
Lots of built in apps
The phone comes with a huge amount of bundlewares. They are not bad actually but i uninstalled most of them and disabled those that couldn’t be uninstalled. Thanks Android for adding the disable feature.
Charging light
When connected through USB, a small LED is lit. Can’t find a setting to disable it. Have to keep the mobile upside down at during charging.
Face unlock
I saw it got the Face unlock capability. Didn’t want to risk trying it for fear that i might not get back in :3
Verdict:
If you need a phone without anything fancy that is usable without slimming your wallet, I’d recommend this phone. 🙂