I noticed one of my servers is sending more logs than the other. `sshd` was the application sending the most amount of logs in the last 24 hours.
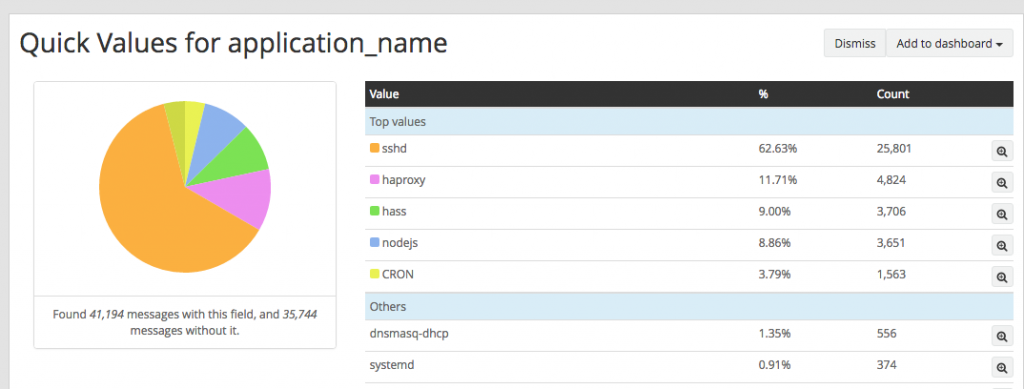
The logs look like these:
pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=116.31.116.52 user=root
Failed password for root from 116.31.116.52 port 14281 ssh2
message repeated 2 times: [ Failed password for root from 116.31.116.52 port 14281 ssh2]
Received disconnect from 116.31.116.52 port 14281:11: [preauth]
Disconnected from 116.31.116.52 port 14281 [preauth]
PAM 2 more authentication failures; logname= uid=0 euid=0 tty=ssh ruser= rhost=116.31.116.52 user=root
Since the IPs are being logged, I can know from where these are coming. Let’s generate a map.
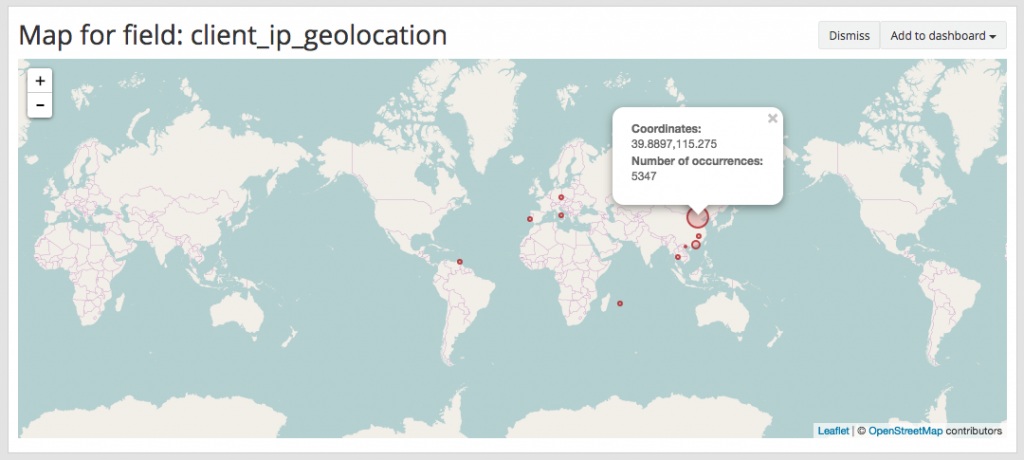
Well well well, 5437 occurrences from China. Gotta do something. Here’s frequency of the attacks this week.
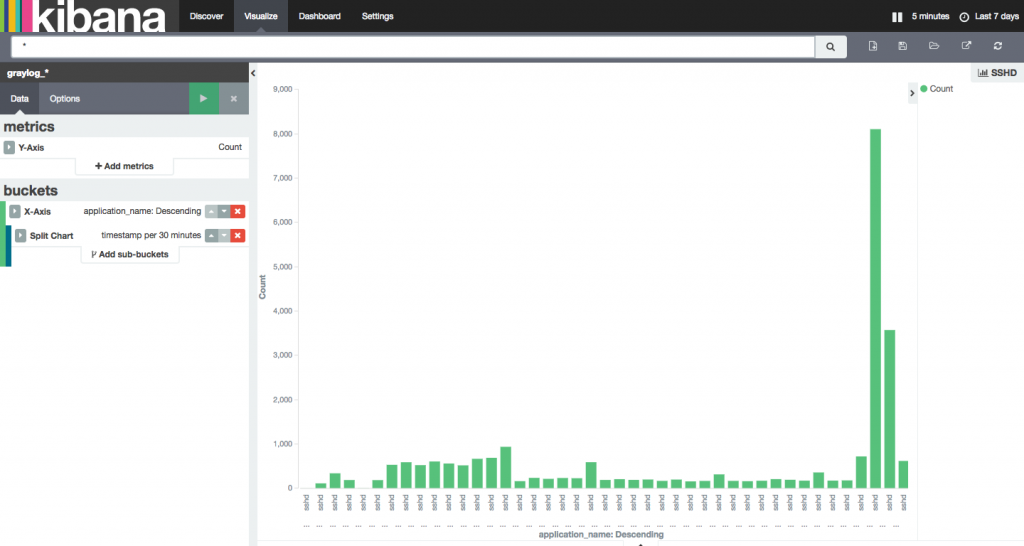
It seems to have amplified today. Looking at the logs, we can see that the were trying different passwords for the user `root`. Lemme just disable password authentication for SSH.
$ vim /etc/ssh/sshd_config
Change the line
#PasswordAuthentication yes
to
PasswordAuthentication no
$ service ssh restart
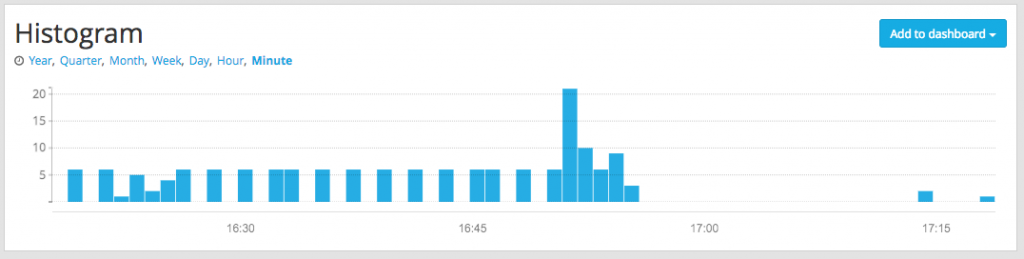
And we can see the logs are no more appearing 😉
Do you wish to analyse your server logs too? Feel free to message me on Facebook or Twitter or LinkedIn